Varied topics in software development and system administration.
Contents
Preventing brute-force attacks in WordPress
A brute-force attack is an attempt to guess the passwords for user accounts by trying many passwords or passphrases sometimes from hundreds of different IP addresses. Since each subsequent request appears to come from a different IP address it could be difficult to stop these attacks by blocking an IP address after several failed attempts.
One possible approach is to block an IP address after the first failed attempt to guess the password for one of the known privileged accounts like admin or administrator.
Add the following action to a WordPress theme or plugin:
function wp_login_failed_action ($username) {
error_log ("[{$_SERVER["REMOTE_ADDR"]}] Login failed: $username");
}
add_action ("wp_login_failed", "wp_login_failed_action");
Add a fail2ban filter. An example below is for the php-fpm log on EL6.
[Definition] failregex = ^\[\] \[<HOST>\] Login failed: (admin|administrator)$ ignoreregex =
Now you can use this filter in your jail configs. Also recommended:
- Whitelist the IPs you use to access these privileged accounts.
- Add to the filter other usernames used by the attackers.
- Do not post under any of the usernames being used for administration.
- Exclude privileged accounts from sitemaps.
- Use strong passwords.
- Use CAPTCHAs.
Note: Following this approach you may inadvertently block a proxy server used by a large group of potential visitors.
Fail2ban and null routing
Null routing has an advantage over classic firewalls since it is available on every potential network router and adds virtually no performance impact. Unfortunately stock EL6 fail2ban package does not support null routing out of the box but this can be fixed in a few simple steps.
Add a new fail2ban action definition:
[Definition] actionban = ip route add blackhole <ip> actionunban = ip route del blackhole <ip>
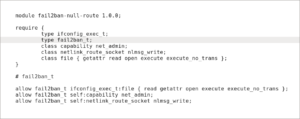
Compile and install a local policy module using the following type enforcement file:
module fail2ban-null-route 1.0.0;
require {
type ifconfig_exec_t;
type fail2ban_t;
class capability net_admin;
class netlink_route_socket nlmsg_write;
class file { getattr read open execute execute_no_trans };
}
# fail2ban_t
allow fail2ban_t ifconfig_exec_t:file { read getattr open execute execute_no_trans };
allow fail2ban_t self:capability net_admin;
allow fail2ban_t self:netlink_route_socket nlmsg_write;
Run these commands in the directory where you created the above type enforcement file:
# make -f /usr/share/selinux/devel/Makefile
# semodule -i fail2ban-null-route.pp
Now you can use null routing in your jail configs:
...
[exim]
enabled = true
findtime = 86400
maxretry = 3
action = null-route
mail-whois[name=exim]
...
Related articles
WordPress 5.4 on CentOS 6
WordPress 5.6 on CentOS 6
Broken WooCommerce reviews in the Dashboard







